Welcome to Six Industries of Arizona
At Six Industries, we are redefining the future of battle management and application solutions. As a leader in cutting-edge technology, we specialize in developing advanced software and applications designed to enhance decision-making, operational efficiency, and mission success.
About Company
Our C5ISR expertise ensures seamless integration of data
Communication, and actionable intelligence, empowering defense and aerospace industries with unparalleled precision and reliability.
From innovative software development to tailored application solutions, Six Industries is your partner in navigating the complexities of modern battlefields. Explore the power of technology with us—where innovation meets strategy.
Our Specialties
At Six Industries of Arizona, we pride ourselves on delivering cutting-edge solutions tailored to the needs of modern defense and aerospace industries.
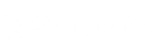
Our flagship product, Tertia Optio, embodies these specialties, offering a modern alternative to traditional battle trackers with enhanced security and functionality.
Copyright © 2025 Six Industries of Arizona. All rights reserved.